Documenting data breaches
Why paper and spreadsheets may not be enough …
A Breach Scenario
You’ve experienced a breach where information was sent to the wrong person. During the investigation it became clear that the person whose data was breached was aware of it happening. You took the actions that seemed appropriate and decided that it wasn’t necessary to report to the Information Commissioner’s Office (ICO). Case closed.
This is a situation that you might recognise and it’s a pattern that many breaches follow.
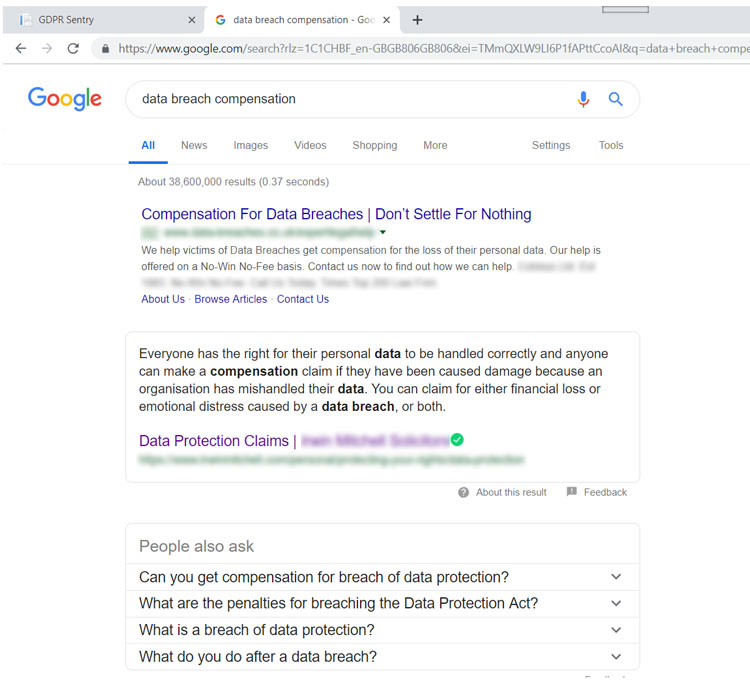
If you type ‘data breach’ into a search engine like Google, high in the list of predicted searches is ‘Data breach compensation’. On the pages this search returns you’ll find law firms letting people know about their right to compensation. This compensation can cover both direct losses and emotional distress. It’s very hard to demonstrate that someone didn’t experience distress. You’ll also see that some firms are focused on ‘public authorities’ including schools for raising these claims.
If someone makes a claim it can be strengthened by making a complaint to the ICO. This is quite a simple process although it may take some time. If you’ve provided even fairly basic information to the data subject about what has happened this may be enough for the ICO to make a determination. The first you hear about it may be when you’re informed of the decision.
Managing the details
It would great to think that if you can prevent breaches from ever happening then the problem would be solved. While a breach free world would be excellent it’s not the real world, breaches do happen. Of course it’s important to put measures in place to reduce the risks of breaches occurring, but it’s also important to pay attention to what happens when they do.
You can have the best measures in place, but if you can’t demonstrate them then they won’t help if a complaint arises.
Legal requirement
The time limit for a claim is six years and breach records should therefore be retained for this period of time.
Paper and spreadsheets
There is a risk that using paper and spreadsheets may simply not provide the required level of documentation and could significantly increase the level of risk from a potential claim down the line.
System – Keep track of your actions
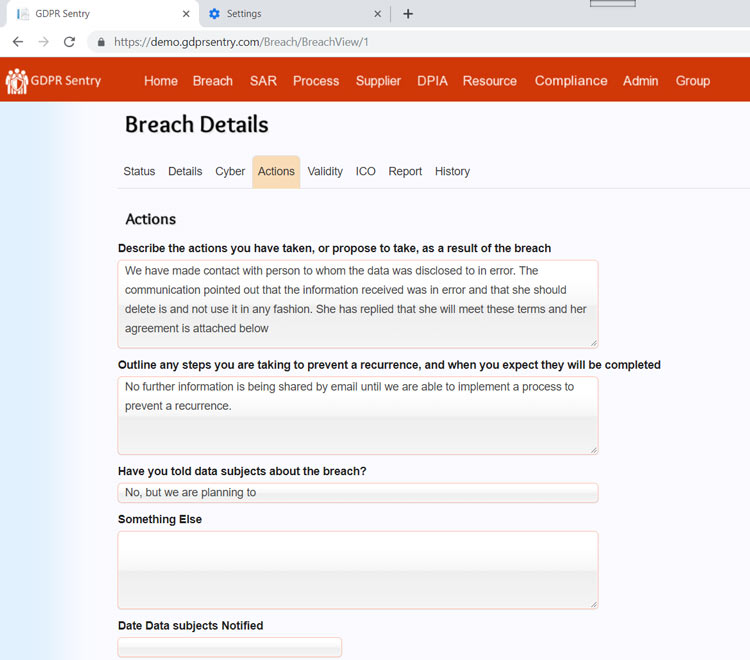
By using a system you can fully document the action that you’ve taken around a breach incident including communicating with data subjects. You can create a timeline, add notes and attachments so that all the information is to hand, whenever you need it.
This is where the Sentry system can help
More Information
GDPR Sentry Limited
Unit 434 Birch Park
Thorp Arch Estate
Wetherby
West Yorkshire
LS23 7FG
0113 804 2035
info@gdprsentry.com
Registered in England under Company Number: 11093693
